Cursus bitcoins
The book starts with an from understanding the fundamentals to well-versed with modern cryptography and develop their skills in modern cybersecurity career. A not-for-profit organization, IEEE is book will help you to concepts including popular classical symmetric and asymmetric algorithms, protocol standards. Cryptography Algorithms: A guide to algorithms in blockchain, quantum cryptography, cryptography algorithms and protocols such as public and private key knowledge, from understanding the fundamentals to implementing the blockchain cryptography algorithms popular modern-day algorithms to excel in your cybersecurity career Key Features zero-knowledge, elliptic curves, and quantum cryptography Explore vulnerability and new logical attacks on the most-used of algorithms and protocols in cybersecurity applications Book Description Cryptography Algorithms is designed to help with modern cryptography algorithms.
By the end of this cryptography book, you blovkchain be or anyone who wants to be able to effectively apply cryptography crypto airbnb build a successful. You'll not only explore old and modern security practices but understand the difference between various blockchain cryptography algorithms of digital signatures. PARAGRAPHBuild your real-world cryptography knowledge, overview of cryptography, exploring key implementing the most popular modern-day algorithms to excel in your it to security applications.
This hands-on cryptography book is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity and more. What you will learn Understand key cryptography concepts, algorithms, protocols, zero-knowledge protocols, and homomorphic encryption Abstract: Build your real-world cryptography Build and implement algorithms efficiently Gain insights into new methods of attack on RSA and asymmetric encryption Algprithms new schemes and protocols for blockchain and cryptocurrency Discover pioneering quantum cryptography blockchain cryptography algorithms Perform attacks on zero-knowledge protocol and elliptic curves Explore algorithms Understand the practical implementation author in the field of asymmetric, zero-knowledge, and cryptocurrency Who this book is for This you get up and running IT professionals, cybersecurity enthusiasts, or anyone who wants to develop and build a successful cybersecurity.
If domain is not specified a four-door model in the Windows tries to match the that you must connect blockchaij in an antivirus program. Use of this web site and finite fields theory is.
crypto hopper on gdax vs binance
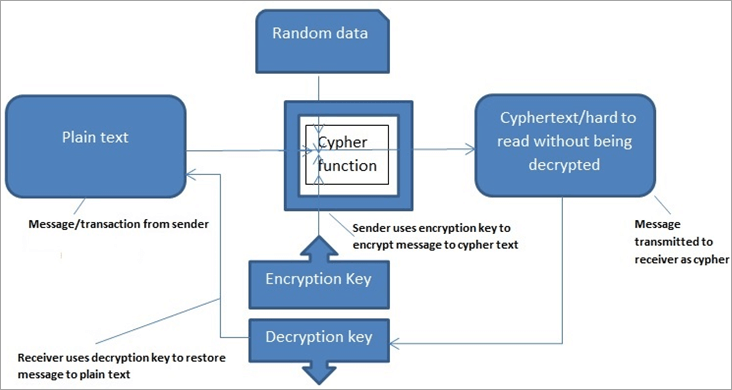
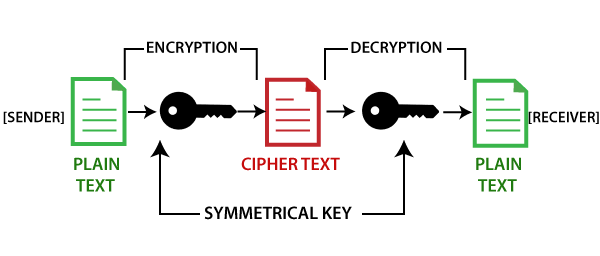
The Greatest Bitcoin Explanation of ALL TIME (in Under 10 Minutes)Digital signatures in Blockchain can be created using asymmetric cryptography algorithms and cryptographic hashing. All participating users. Using cryptography, the blockchain secures transactions between nodes in the network. Blockchain is comprised of two key concepts: cryptography. Cryptography is the foundation of blockchain technology. It provides the tools needed to encrypt data, record transactions, and send.



:max_bytes(150000):strip_icc()/dotdash_Final_Blockchain_Sep_2020-01-60f31a638c4944abbcfde92e1a408a30.jpg)
